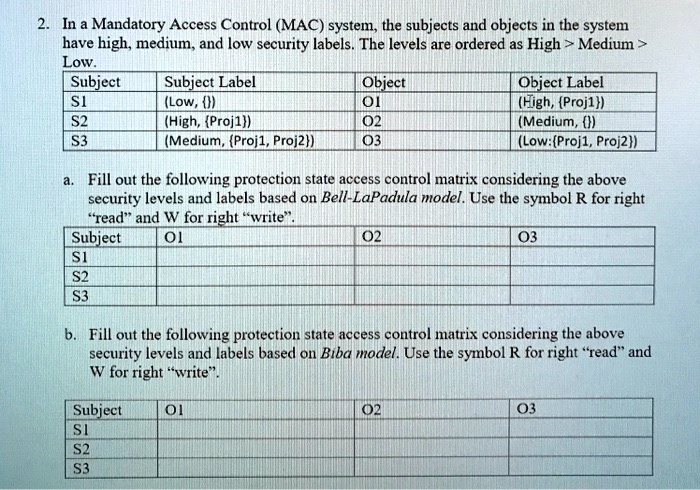
44 security labels access control
How security labels control access - help.hcltechsw.com Security labels rely on security label components to store information about the classification of data and about which users have access authority. Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). Using Security Labels for Directory Access and Replication Control - Isode The access control model is that a Security Label is associated with each entry in the directory, and that label indicates the sensitivity of the information contained in the directory entry. The example DIT "organizations", with different Security Labels.
Access Control using Security Labels & Security Clearance - Isode Security Labels and Security Clearance provides a mechanism for controlling access to information that works well for large numbers of users. It can be an effective approach for access control in organizations that do not use non-electronic security labels. The following diagram shows the translation of the earlier example into electronic form.
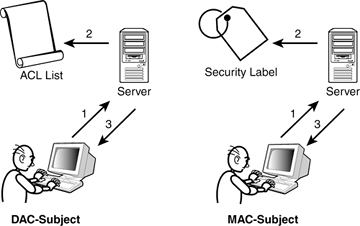
Security labels access control
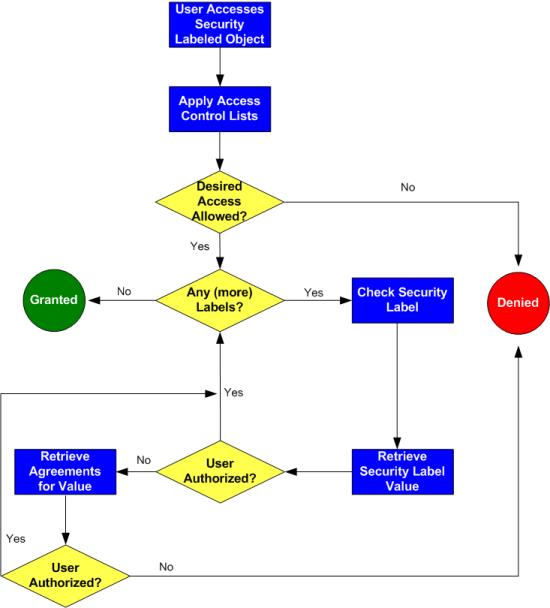
Cloud Video Surveillance & Access Control - Atlanta, Georgia | ControlByNet Ensure. Resident Safety and Minimize Risk. to Owners. ControlByNet offers many options to ensure your risk is under control and that you have the latest software and benefits at your browser fingertips. We developed the surveillance solution specific to the Multifamily industry and it is trusted by many communities across the nation. Security Labels and Access Control - support.ptc.com To access an object, a user must be cleared for all security labels, either as an authorized participant or by an active agreement, and have proper access control permissions for that object. The following flow chart provides an overview of how Windchill processes security labels and access control to grant or deny a user access to an object. Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values
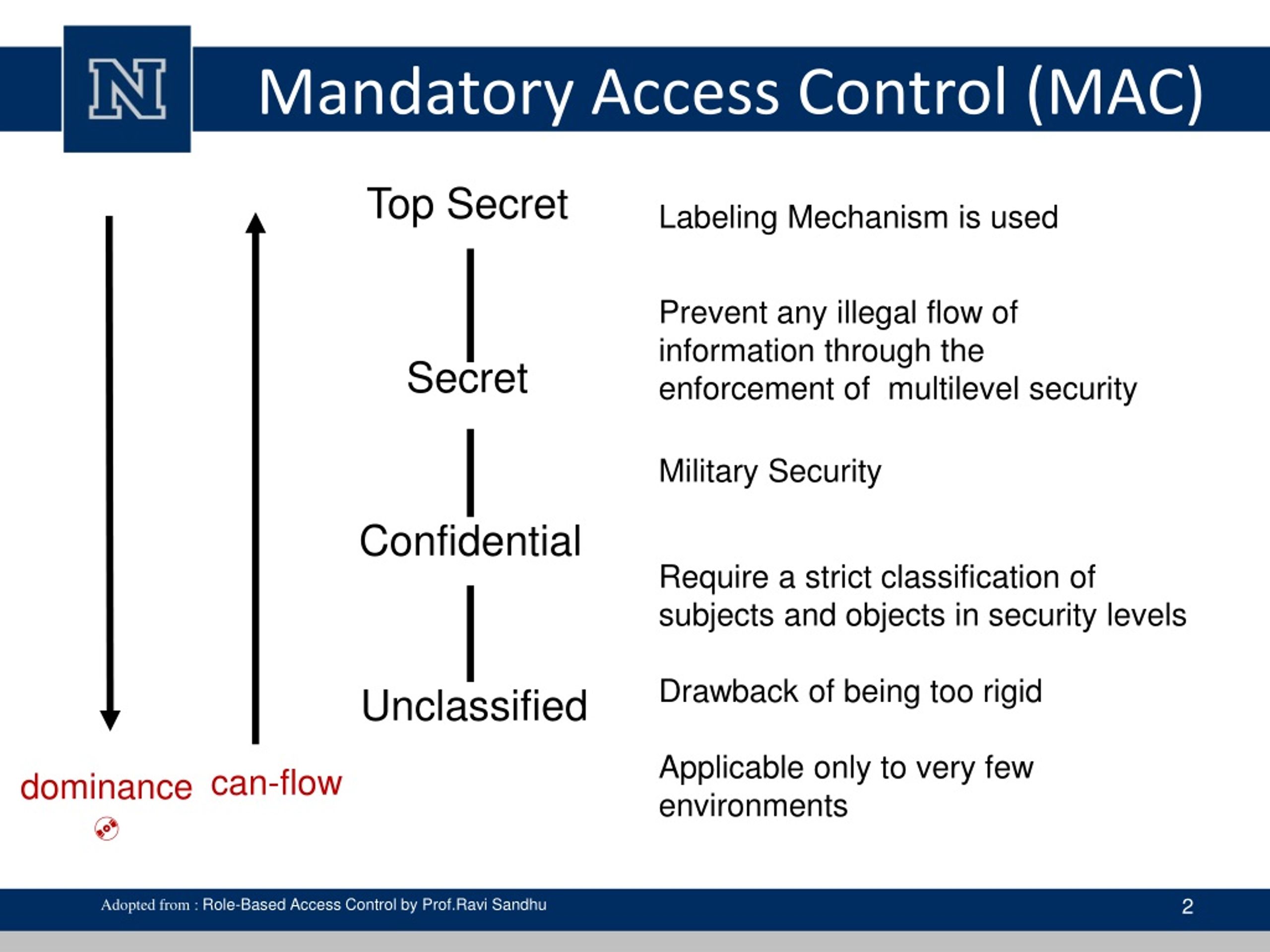
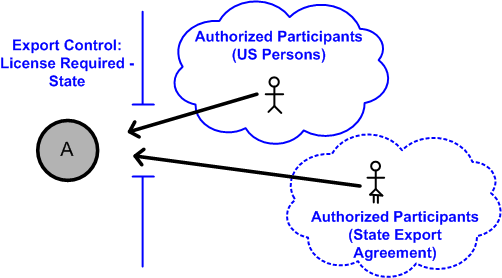
Security labels access control. Security Labels Overview - PTC Uniquely configured by each site, security labels work with the Windchill access control policies and ad hoc permissions for an object to determine whether a user is authorized to access an object. A site can configure multiple security labels to cover various needs, such as identifying legal information, establishing export control criteria, or protecting proprietary information. en.wikipedia.org › wiki › Mandatory_access_controlMandatory access control - Wikipedia Access to the labels and control mechanisms are not [citation needed] robustly protected from corruption in protected domain maintained by a kernel. The applications a user runs are combined with the security label at which the user works in the session. Access to information, programs and devices are only weakly controlled [citation needed]. learn.microsoft.com › en-us › securityAzure security baseline for Azure Kubernetes Service ... Jul 07, 2022 · Identity and Access Control. For more information, see the Azure Security Benchmark: Identity and Access Control. 3.1: Maintain an inventory of administrative accounts. Guidance: Azure Kubernetes Service (AKS) itself does not provide an identity management solution which stores regular user accounts and passwords. With Azure Active Directory ... Physical Access Control - CardWerk software for smart cards Our expertise extends to both logical AND physical access control. Ask for our "One Badge Fits All" design, which merges physical and logical access security. The same credential can be used to access a building and your computer system. Cyber security is greatly improved adding secure email, logon, single sign on and many more security ...
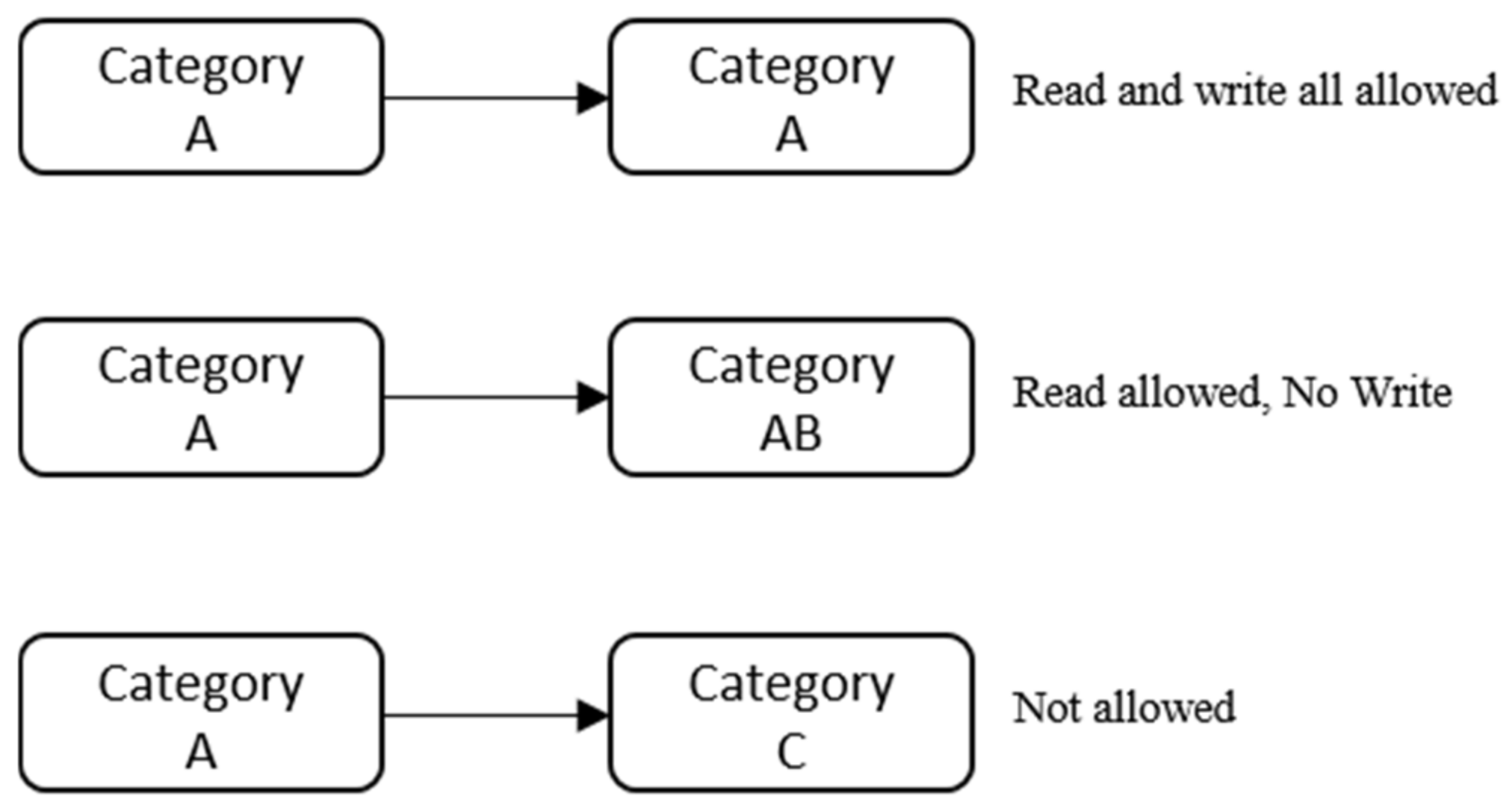
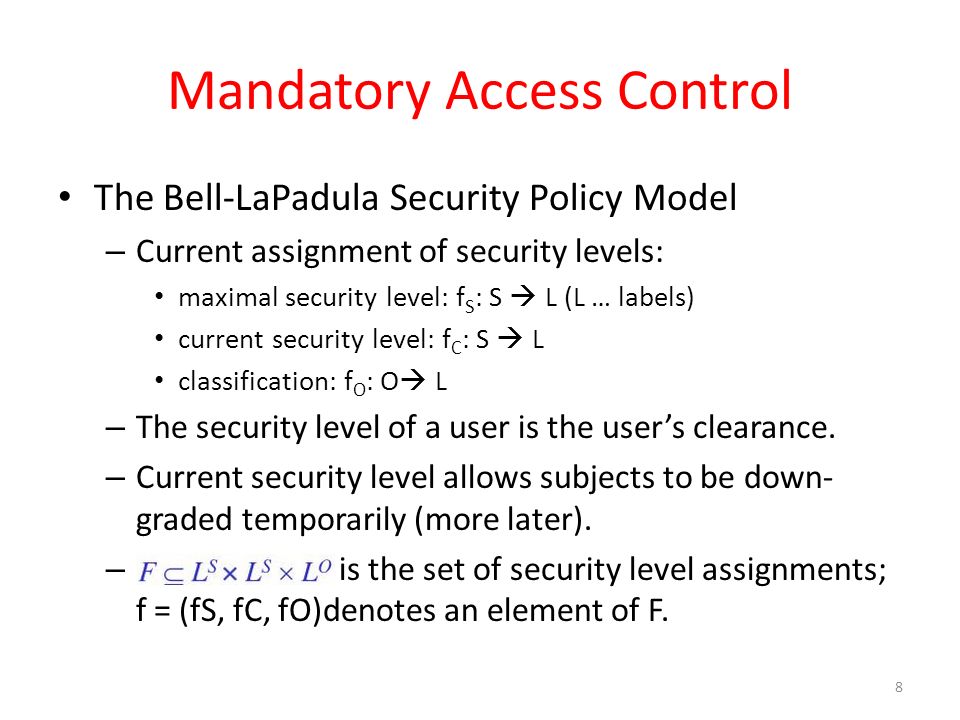
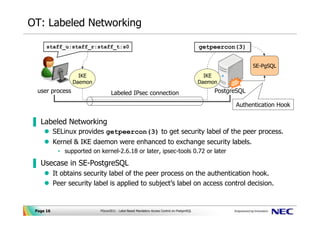
learn.microsoft.com › en-us › microsoft-365Permissions - Security & Compliance Center - Office 365 Sep 27, 2022 · These people can perform only the tasks that you explicitly grant them access to. To access the Security & Compliance Center, users need to be a global administrator or a member of one or more Security & Compliance Center role groups. Permissions in the Security & Compliance Center are based on the role-based access control (RBAC) permissions ... Label-Based Access Control security labels, which control access to protected tables. Security policies Security policies are database objects that you create and use to protect tables from unauthorized access. Security labels Security labels are objects applied to rows and columns in order to protect these data, and granted to users to give them access to protected data. Access Control Models: MAC, DAC, RBAC, & PAM Explained MAC works by applying security labels to resources and individuals. These security labels consist of two elements: Classification and clearance — MAC relies on a classification system (restricted, secret, top-secret, etc.) that describes a resource's sensitivity. Users' security clearances determine what kinds of resources they may access. en.wikipedia.org › wiki › Access_controlAccess control - Wikipedia The term access control refers to the practice of restricting entrance to a property, a building, or a room to authorized persons. Physical access control can be achieved by a human (a guard, bouncer, or receptionist), through mechanical means such as locks and keys, or through technological means such as access control systems like the mantrap ...
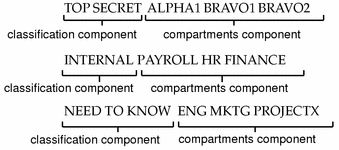
EOF kubernetes.io › docs › conceptsPod Security Admission | Kubernetes Aug 05, 2022 · Pod Security admission places requirements on a Pod's Security Context and other related fields according to the three levels defined by the Pod Security Standards: privileged, baseline, and restricted. Refer to the Pod Security Standards page for an in-depth look at those requirements. Pod Security Admission labels for namespaces cloud.google.com › bigquery › docsAccess control with IAM | BigQuery | Google Cloud Oct 03, 2022 · Predefined roles are meant to support common use cases and access control patterns. Custom roles provide access according to a user-specified list of permissions. To determine if one or more permissions are included in a role, you can use one of the following methods: The IAM permissions search reference; The gcloud iam roles describe command How security labels control access - informix.hcldoc.com Label-based access control (LBAC) works by comparing the labels that you have associated with users against labels that you have associated with data by using a predefined rule set (IDSLBACRULES). You construct these labels with security label components, which represent different levels of data classification and access authority.
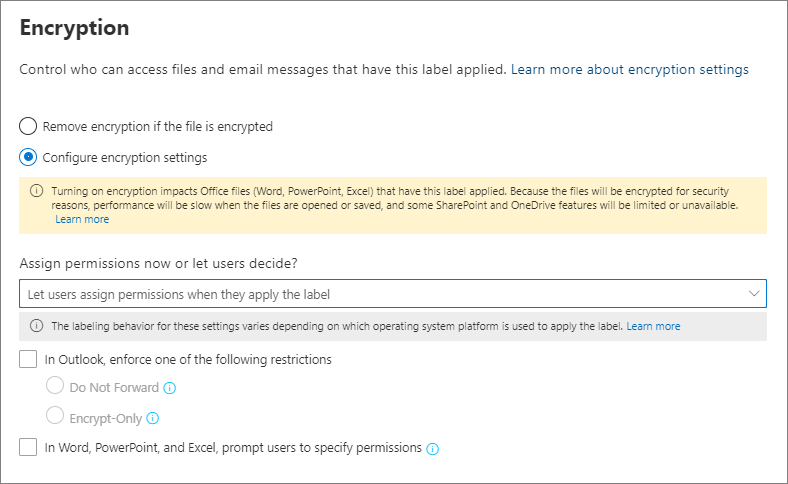
Label Security | Oracle Oracle Label Security Control what data users see based on data and session labels. Oracle Label Security records and enforces access permission for data based on project codes, regions, or data classifications. These controls reduce the risk of unauthorized access to sensitive data and help to demonstrate regulatory compliance.
security alarm technician jobs in Atlanta, GA - Indeed Security/Access Control Technician - Level II. NetPlanner Systems, Inc 3.8. Norcross, GA 30071. $18 - $23 an hour. Full-time. Responsible for the installation, maintenance and repair of security alarm wiring and equipment and access control equipment. Submit all paperwork on time.
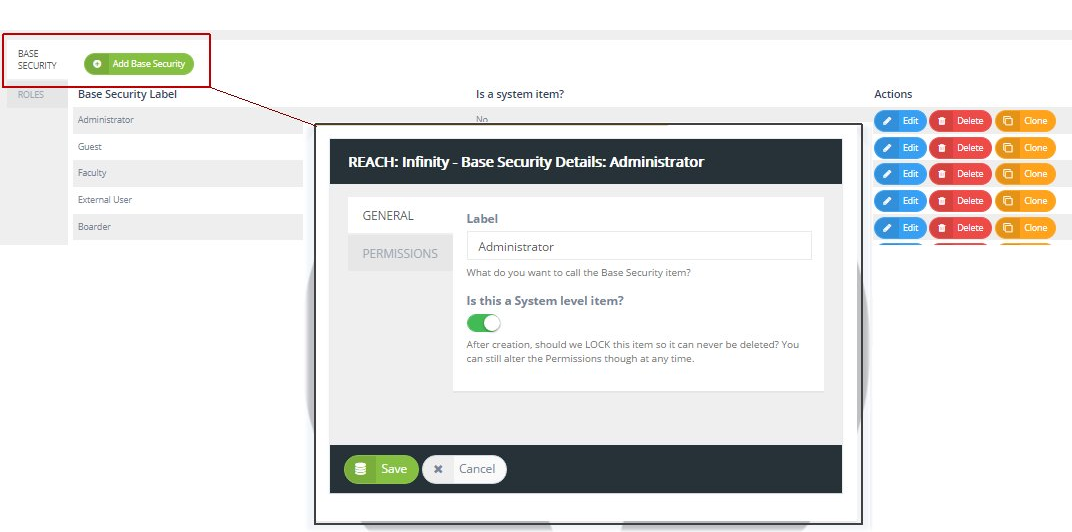
[Knowledge Hub] Windchill PLM Permissions/Access Control/Security Label How to set up security labels? How to troubleshoot access control issues? Log in eSupport Login: Close: Username (Email Address) Password; Invalid username or password Cancel: Forgot password? Create a new account: Support ... Windchill PLM Permissions/Access Control/Security Label Modified: 24-Aug-2022 Applies To Windchill PDMLink 10.0 to 12.0 ...
How security labels control access Home; Security You can secure your HCL OneDB™ database server and the data that is stored in your HCL OneDB™ databases. You can encrypt data, secure connections, control user privileges and access, and audit data security. Security in HCL OneDB™ The HCL OneDB™ Security Guide documents methods for keeping your data secure by preventing unauthorized viewing and altering of data or ...
Gate Systems - Cornerstone Control Systems 5600 Oakbrook Parkway Suite 240 Norcross, GA 30093 (866) 520-7503 (770) 448-9042; CornerstoneService@cornercs.com (770) 448-5436
en.wikipedia.org › wiki › Computer_access_controlComputer access control - Wikipedia In computer security, general access control includes identification, authorization, authentication, access approval, and audit.A more narrow definition of access control would cover only access approval, whereby the system makes a decision to grant or reject an access request from an already authenticated subject, based on what the subject is authorized to access.
Label-based access control (LBAC) overview - IBM In label-based access control (LBAC) a security label is a database object that describes a certain set of security criteria. Security labels are applied to data in order to protect the data. They are granted to users to allow them to access protected data. Format for security label values
Security Labels and Access Control - support.ptc.com To access an object, a user must be cleared for all security labels, either as an authorized participant or by an active agreement, and have proper access control permissions for that object. The following flow chart provides an overview of how Windchill processes security labels and access control to grant or deny a user access to an object.
Cloud Video Surveillance & Access Control - Atlanta, Georgia | ControlByNet Ensure. Resident Safety and Minimize Risk. to Owners. ControlByNet offers many options to ensure your risk is under control and that you have the latest software and benefits at your browser fingertips. We developed the surveillance solution specific to the Multifamily industry and it is trusted by many communities across the nation.






![PDF] A System for Supporting The Cyber Security Control of ...](https://d3i71xaburhd42.cloudfront.net/e24f299c73998f565a63fa1258a15c55ab10c816/2-Table1-1.png)



















!['Mandatory Access Control Essentials with SELinux': Costas Senekkis, ICSI [CRESTCon 2019]](https://i.ytimg.com/vi/h4eG8y53D9Q/maxresdefault.jpg)

Post a Comment for "44 security labels access control"